Is It Truly "Off Your Network"?
Is It Truly "Off Your Network"?
What sets HoverCam Orbit Pro and Air wireless document cameras apart is their unique ability to operate completely off your network. But why is this "Not-On-Your-Network" feature significant? Simply put, the best network security comes through segmentation. A device isolated from your existing network creates an air gap, preventing any potential breach from spreading to your infrastructure. This is the most effective way to safeguard your network from vulnerabilities in a wireless document camera.
Recently, many wireless document camera vendors have started claiming their devices are "Not-On-Your-Network." To help educators choose the most secure wireless solution, we’ll clarify what it truly means to be off your network and cut through misleading claims.
What Does "On-Your-Network" Mean?
A wireless document camera is on your network if it:
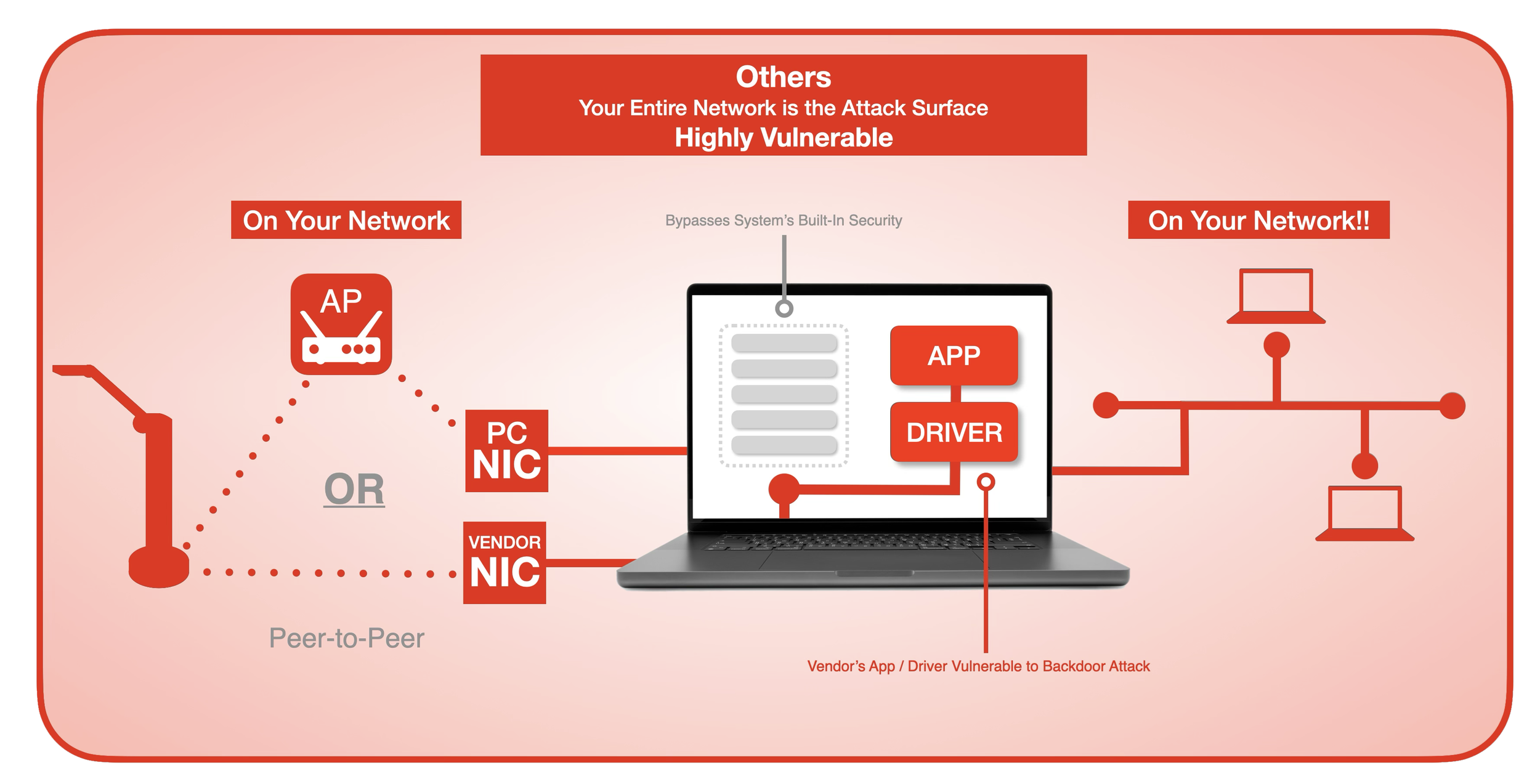
Connects to your host computer through an existing WiFi router or Access Point (AP).
Communicates via a Network Interface Card (NIC), whether it’s the primary NIC or a secondary one installed via a vendor’s USB dongle.
Why does this matter? These devices require the vendor to install a network app or driver on your computer. This software, running on a device connected to your network, is a potential vulnerability. A backdoor or trojan in the app could expose your entire network. As a customer, you can’t realistically scrutinize the vendor’s code. If even Apple’s heavily secured AppleTV was hacked recently, can you trust a document camera vendor to outdo a trillion-dollar company?
The diagram below highlights vulnerabilities in red, illustrating how an on-network wireless camera exposes your entire network to potential attacks.
How to Tell If It’s On Your Network
Ignore buzzwords like “peer-to-peer,” “MiraCast,” “WiFi Direct,” or “separate NIC.” Instead, ask one critical question:
“Do you install any networking app or driver on my computer or display panel?”
For most vendors, the answer is yes—they must install networking code to connect as a network device. This makes them inherently on your network. The exception? HoverCam’s Orbit
Orbit’s Architecture: Truly Off Your Network
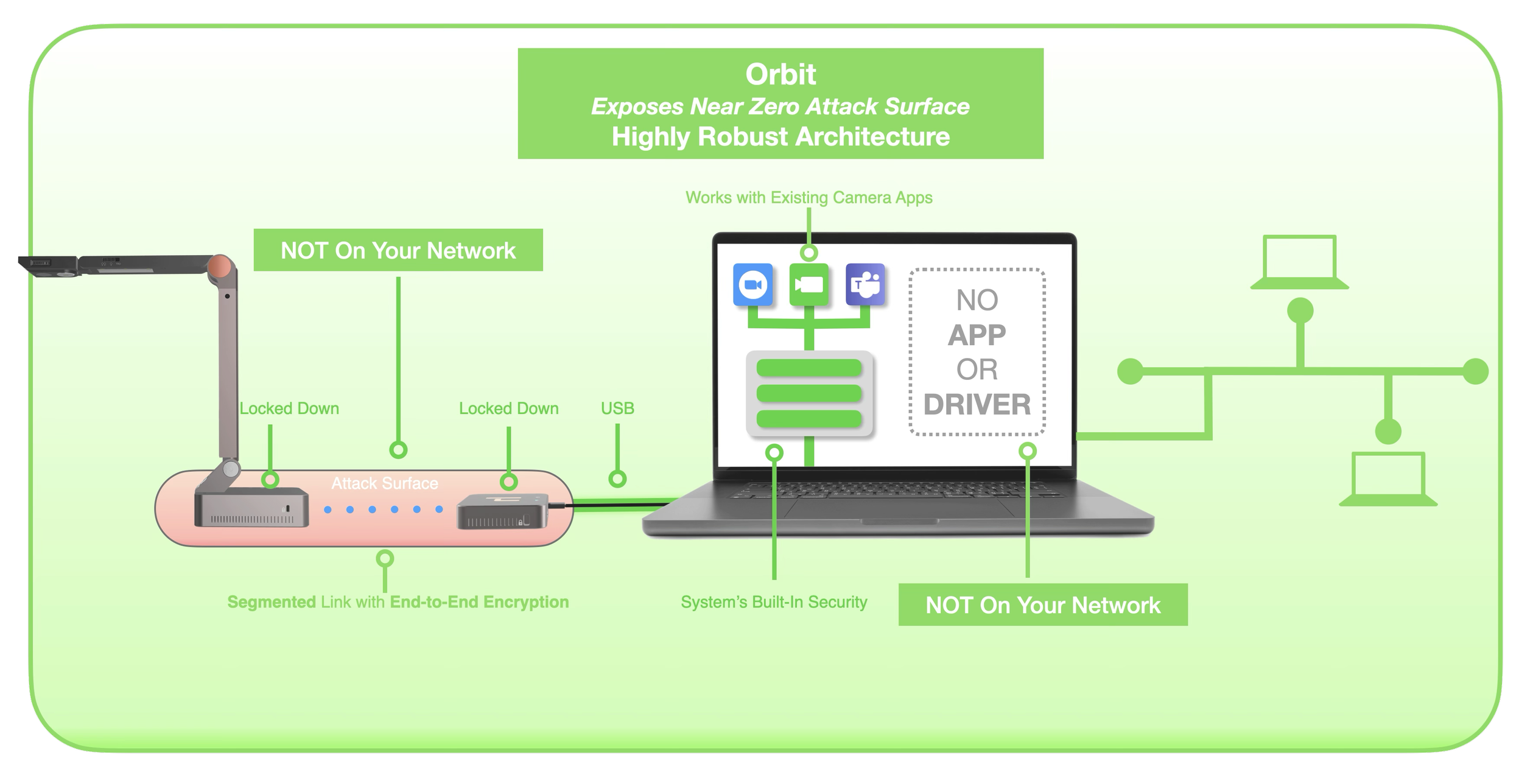
HoverCam’s Orbit Pro and Air are designed from the ground up to operate as an isolated segment, connecting to a host computer or Interactive Flat Panel (IFP) via a wired USB or HDMI cable. Unlike other wireless cameras, Orbit connects as a USB webcam, not a network device.
Key features of Orbit’s security architecture:
No networking drivers or apps required. Orbit uses the generic USB Video Class (UVC) driver built into Windows, macOS, ChromeOS, and Linux.
No interaction with your device’s network stack. Orbit is invisible to your network, with no IP address or open ports.
Encrypted, isolated wireless link. Orbit’s transmitter and receiver communicate over a segmented, encrypted wireless connection. The receiver converts this signal into a standard USB camera input, creating a direct, physical connection outside your device’s network layer.
In simple terms, Orbit’s wireless link terminates before it reaches your computer’s network, creating a “fire gap” at the USB port. This ensures that any potential breach in Orbit’s internal wireless link cannot spread to your network.
By choosing Orbit, you’re opting for a wireless document camera that prioritizes security through true network isolation.
Comparison Table: Orbit vs. Other Wireless Cameras
Based on the security features and architectures discussed, here's a high-level comparison table to illustrate the key differences:
| Feature | Orbit Pro/Air | Other Wireless Cameras |
|---|---|---|
| Network Connection | Not on your network; isolated USB as UVC/UAC/HID device | On your network; connects as network device via Wi-Fi or vendor NIC |
| Required Software/Drivers | None; uses built-in OS generic drivers | Proprietary apps and drivers required, vulnerable to backdoors/Trojans |
| Password Setup | Unique end-to-end encryption per pair; no global/default passwords | Often uses global passwords; single point of failure |
| Attack Surface | Near zero; isolated closed-loop wireless link | High; direct network access leads to potential district-wide breaches |
| Physical Security | mmWave signals confined to room (Pro model) | No such confinement; accessible remotely |
| Vulnerability to Breaches | Breaches isolated from host computer (fire gap via USB) | Direct breach to network via installed code |
| Overall Safety | High; designed for zero network exposure | Low; exposes computers to unaudited risks |
This table underscores why Orbit minimizes risks while others amplify them through network integration.
For more details on HoverCam Orbit Pro/Air, visit the official resources or consult with IT security experts to evaluate your setup.
This post is based on security documentation and architectural comparisons from HoverCam.